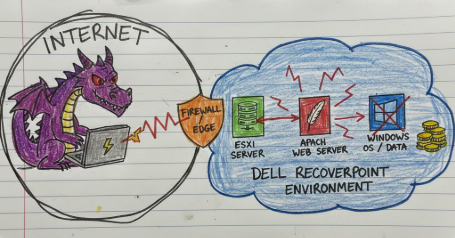
Dell RecoverPoint for VMs (CVE-2026-22769)
Published: Februrary 17, 2026When your backup appliance is also a pre-installed APT welcome mat
GOTT Labs is an independent cybersecurity research project focused on studying how threats operate in practice, how defensive systems respond under real conditions, and where theory quietly diverges from reality.
This site exists to publish research. Any resemblance to marketing is coincidental.
When your backup appliance is also a pre-installed APT welcome mat
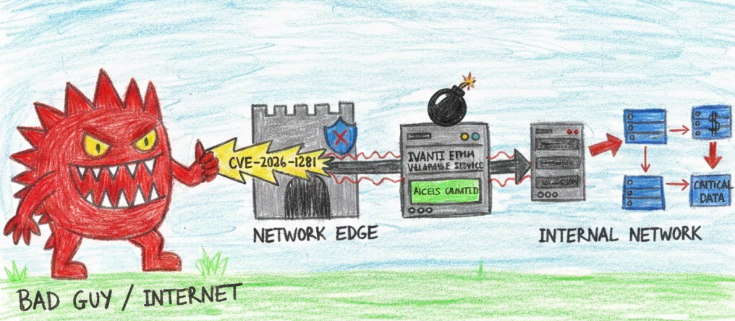
Forensic analysis of pre-auth RCE exploitation in Ivanti EPMM through esoteric shell evaluation mechanics
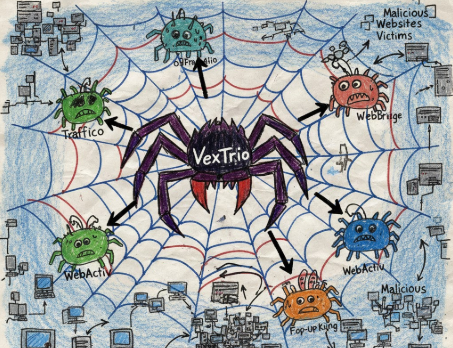
How a Billion-Dollar Cybercrime Operation Hides Behind Legitimate AdTech (Part 1)
MongoBleed, a discussion of forensics and considerations

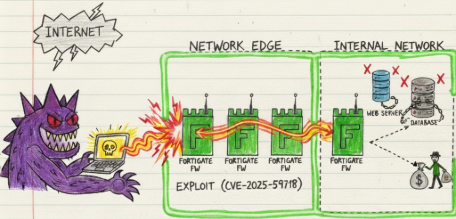
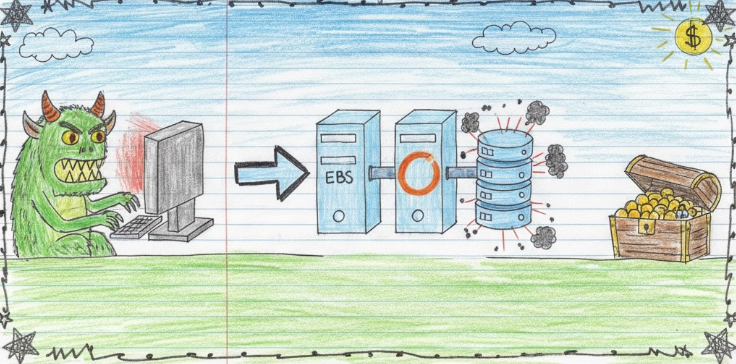
CVE-2025-59718 & CVE-2025-59719 - Who Needs Signature Verification Anyway?
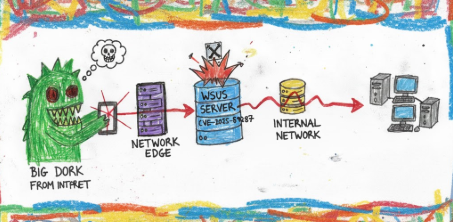
A critical unauthenticated RCE vulnerability that turned Microsoft's patch delivery system into an attacker's dream"
The Zero-Day That Reminded Everyone Why ERP Means "Everyone's Really Pwned"
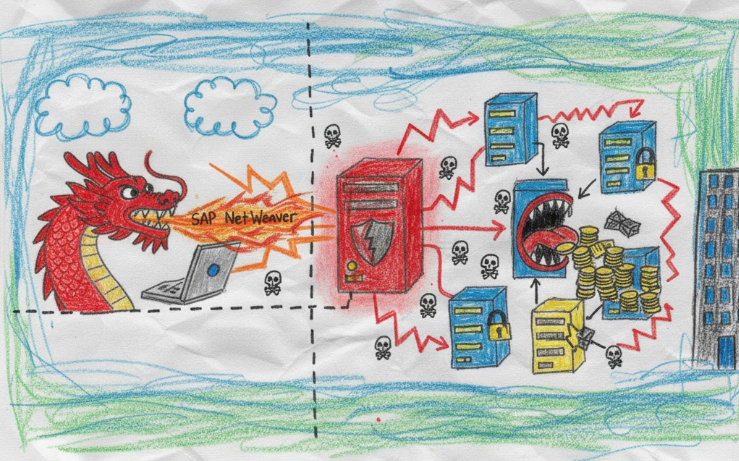
How an obscure endpoint turned SAP NetWeaver into a webshell wonderland
When authentication is just a really aggressive suggestion
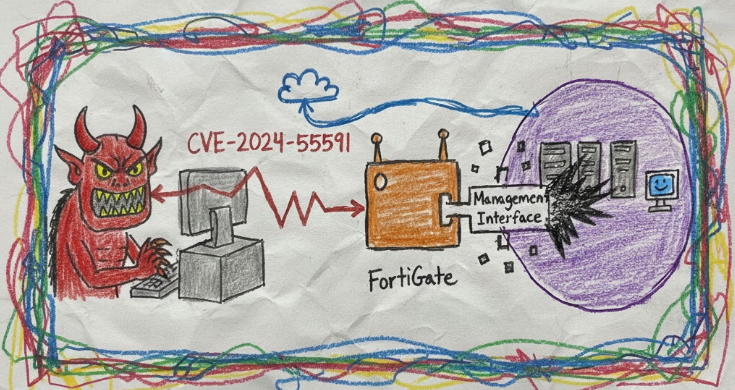
When Your Security Appliance Becomes the Vulnerability

How Missing Auth in FortiManager Let UNC5820 Play Musical Chairs with Enterprise Networks
How ex-Conti operators are extorting millions without writing a single line of malicious code

When 32 Null Bytes Break Authentication and SIEM Logs Miss Everything That Matters
Research published is provided for educational purposes. Findings reflect observed behavior in specific environments and should not be interpreted as universal truth, vendor endorsement, or operational guidance. Techniques discussed may be incomplete, ineffective, or rendered obsolete without notice. Readers are expected to apply judgment, skepticism, and basic security hygiene.